AWS Identity Access Management (IAM):
Note: A root account is created automatically when you sign up for AWS. It shouldn’t be used for daily operations and shouldn’t be shared.
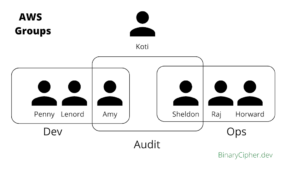

Permissions:
- In AWS Users and Groups can be assigned JSON documents called policies
- These policies define user permissions
- In AWS you apply the least privilege principle, Don’t give permission more than the user needs.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "cloudtrail:GetTrail",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"iam:GenerateServiceLastAccessedDetails",
"iam:GetServiceLastAccessedDetails"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::{{cloudtrail-bucket}}",
"arn:aws:s3:::{{cloudtrail-bucket}}/*"
]
},
{
"Effect": "Allow",
"Action": [
"kms:Decrypt"
],
"Resource": [
"arn:aws:kms:{{region}}:{{account}}:key/{{key}}"
],
"Condition": {
"StringLike": {
"kms:ViaService": "s3.*.amazonaws.com"
}
}
}
]
}
IAM Policy structure:
The policy JSON consists of the Policy version, ID and statement
Policy version is the policy language version ex: “Version”: “2012-10-17”,
Statement is one or more individual statements consisting of definition of the policy
Statement
The statement consists of Effect, Action, Resource, and sometimes Condition
- The effect contains what is the effect on the action items such as “Allow” “Deny”
- Action defines what type of operations or actions can the user person on a service. for example, get users list, create user
- The resource is nothing but the AWS service there are many services AWS offers each one is a resource that user can do operate on them.
- The condition is to specify what specific condition the user can do these operations on a service. These conditions are handy when you want to restrict users specific to certain project-specific within a service.
AWS Roles for Services:

AWS roles are used to person actions on behalf of user by an AWS service. For example, an AWS Ec2 instance wanted to person an operation using AWS Service, and it requires permission to do so, for that purpose, we use AWS roles for service.
AWS CLI:
- A tool that enables you to interact with AWS via the command line. It’s an alternative to the web management console.
- You can download it from https://github.com/aws/aws-cli
- If you want your web version without installation, you can use AWS
- Install on Mac/widows/Linux from https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html
- Once installed, open the command line and check
aws --version - You’ll get the following response
aws-cli/2.8.12 Python/3.9.11 Darwin/22.1.0 exe/x86_64 prompt/off
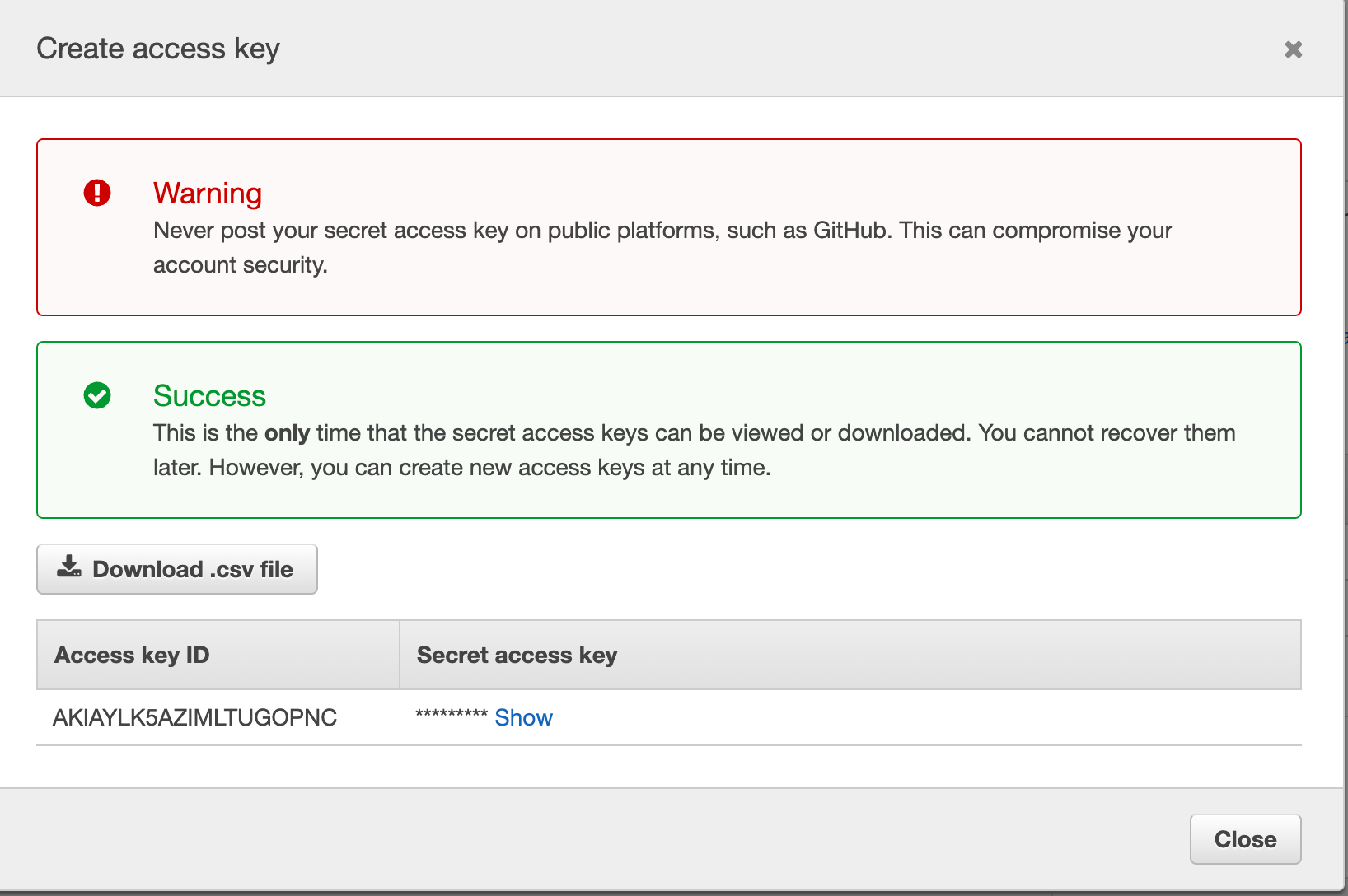
To access AWS from CLI you need to create an access key
- To create access key naviage to IAM and users
- Select the user you want to create an access key an click on “Security credentials” tab
- Click on create access key button
- It’s only once shows on the screen take note of both ID and secret and download the .csv file
- Go to AWS CLI and hit
aws configure - AWS Access Key ID [None]: <AWS ID>
- AWS Secret Access Key [None]: <KEY>
- Default region name [None]: us-east-1 <AWS region>
- Default output format [None]:
Now you should be able to access AWS from the console.
Hit aws iam list-users to list all the users (Note: Only if the logged in user has read access to IAM then only will list any users)
{
"Users": [
{
"Path": "/",
"UserName": "kotidev",
"UserId": "AIDAYLD5AZIMMIFSFPTWP",
"Arn": "arn:aws:iam::574110091800:user/kotidev",
"CreateDate": "2022-06-22T23:40:36+00:00",
"PasswordLastUsed": "2022-11-13T16:06:39+00:00"
}
]
}
To open the Cloudshell command on the web browser login into AWS and click on the command line button in the top right corner

or open: https://console.aws.amazon.com/cloudshell/home
IAM Security tools:
- IAM Credential report (account-level) – A report that contains list of users and their account status
- IAM Access Adviser (user-level) – The report shows the user’s permission granted to services and shows the least used services.
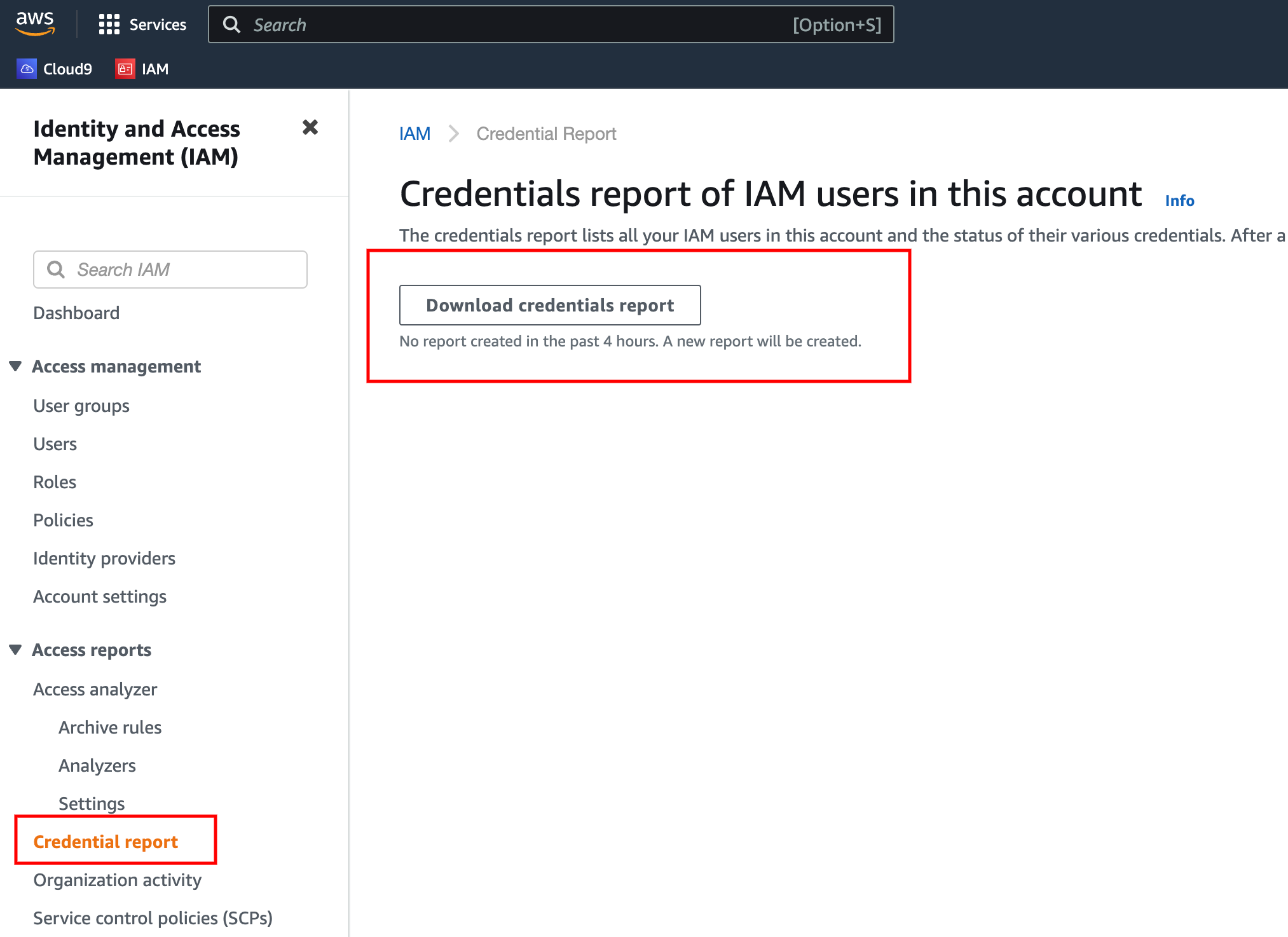

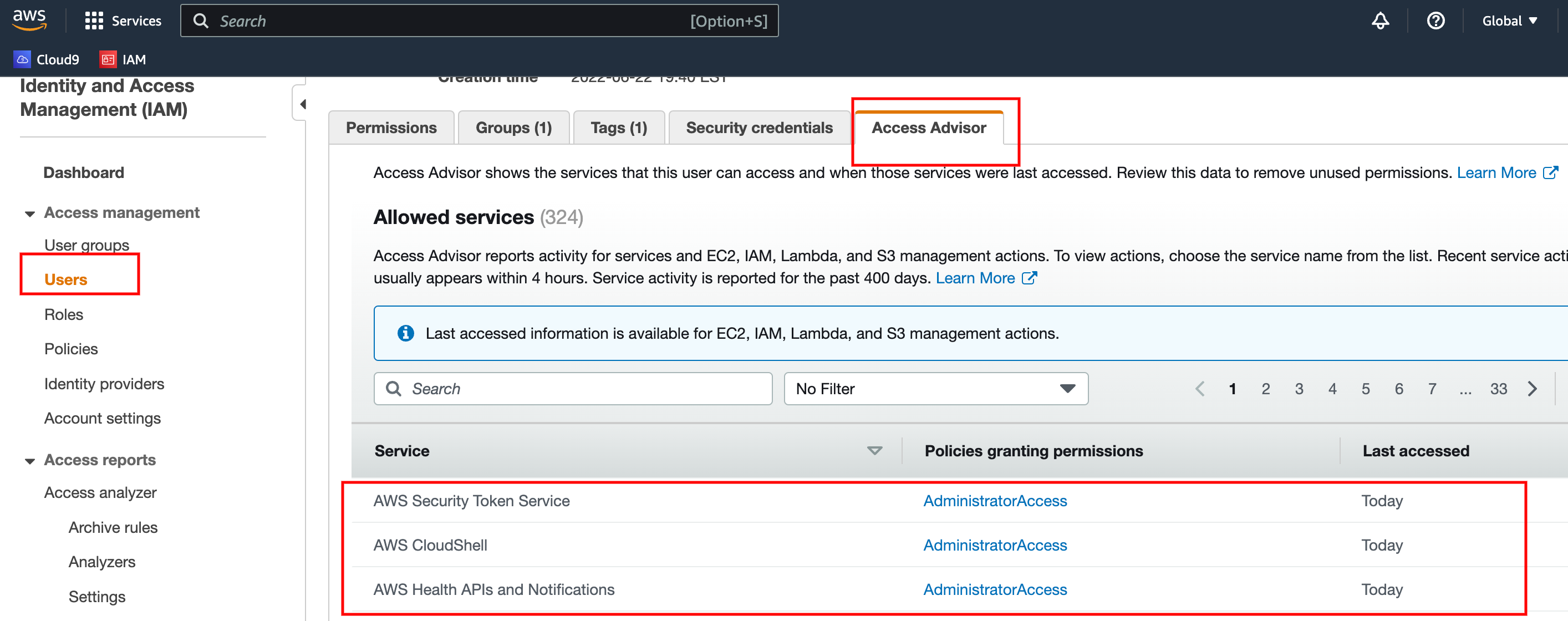

It helps to decide administrators to remove unwanted user permissions and maintain the thumb rule of
“Provide least privileges to any user that required for user certain operation on AWS”
Best practice
AWS SDK:
- AWS SDK is a software development kit that enabled developers to embed AWS services within their applications.
- It enabled you programmatically connect and control AWS services.
- It supports multiple languages (python, Javascript, java… etc.) and provides language-specific APIs
- Example AWS CLI built on the AWS SDK for python.
IAM Best practices
- One user one account
- Do NOT use the root account.
- Assign users to groups and assign permission to groups. Inline policies for users are not a good practice.
- Create a strong password policy
- Use MFA for secure authentication.
- Create roles for assigning permissions to AWS services
- Use access keys for programmatic access to AWS (CLI/SDK)
- Audit permissions of AWS using Credential manager and Access Advisor.
- Never ever share IAM users and Access keys.
Reference: https://aws.amazon.com/iam/
 Binary Cipher
Binary Cipher